PC hardware and software
PC Hardware
- CPU (Central Processing Unit): The brain of the computer, responsible for executing instructions and performing calculations. Popular brands are Intel and AMD.
- GPU (Graphics Processing Unit): Handles rendering of images and videos. Essential for gaming, video editing, and other graphics-intensive tasks. NVIDIA and AMD are key players here.
- RAM (Random Access Memory): Temporary storage that the CPU uses to store and quickly access data. More RAM allows for better multitasking and smoother performance.
- Storage: Includes Hard Drives (HDDs) and Solid State Drives (SSDs). SSDs are faster and more reliable but can be more expensive. HDDs offer more storage for a lower cost.
- Motherboard: The main circuit board that connects all the components. It houses the CPU, RAM, storage devices, and other peripherals.
- Power Supply Unit (PSU): Provides power to all components. It’s important to choose a PSU with adequate wattage for your system’s needs.
- Case: Encloses and protects all the components. It comes in various sizes (ATX, Micro-ATX, Mini-ITX) and styles.
- Cooling: Includes fans, heatsinks, and sometimes liquid cooling systems. Essential for maintaining optimal operating temperatures.
PC Software
- Operating System (OS): The software that manages hardware and provides services for other software. Common OSs are Windows, macOS, and Linux.
- Drivers: Software that allows the operating system to communicate with hardware components. Keep drivers updated for optimal performance and compatibility.
- Antivirus Software: Protects against malware and other security threats. Examples include Norton, McAfee, and Bitdefender.
- Productivity Software: Includes word processors (Microsoft Word, Google Docs), spreadsheets (Excel, Google Sheets), and presentation software (PowerPoint, Google Slides).
- Web Browsers: Software for accessing the internet. Popular options are Google Chrome, Mozilla Firefox, and Microsoft Edge.
- Media Players: Software for playing audio and video files. VLC Media Player and Windows Media Player are common examples.
- Games and Specialized Applications: Includes anything from casual games to professional software for design, programming, and more.
- Utilities: Tools for system maintenance and optimization, such as disk cleanup, defragmentation, and system monitoring software.
Difference between hardware and software
| Aspect | Hardware | Software |
|---|---|---|
| Definition | Physical components of a computer or system | Programs and data that instruct hardware |
| Examples | CPU, GPU, RAM, hard drives, motherboards, keyboards | Operating systems (Windows, macOS), applications (Microsoft Office, Photoshop), drivers |
| Function | Provides physical infrastructure for operation | Provides instructions and user interface for hardware |
| Characteristics | Tangible, can be touched, wears out over time | Intangible, cannot be touched, can be updated or reinstalled |
| Upgrading/Replacement | Physical components can be replaced or upgraded | Software can be updated, modified, or replaced |
Identify various Components on Mother Board

A motherboard is the central circuit board of a computer, and it houses and connects various components. Here are the key components typically found on a motherboard:
1. CPU Socket
- Description: The slot where the CPU (Central Processing Unit) is installed.
- Types: Different types for different CPU manufacturers (e.g., Intel’s LGA, AMD’s AM4).
2. RAM Slots (DIMM Slots)
- Description: Slots for installing RAM (Random Access Memory) modules.
- Types: DDR4, DDR5, etc., depending on the motherboard.
3. Chipset
- Description: A set of chips that manage data flow between the CPU, RAM, and other components. Includes the Northbridge and Southbridge chips in older designs or a single chipset in modern motherboards.
4. PCIe Slots
- Description: Expansion slots for adding additional components like GPUs (Graphics Processing Units), sound cards, or network cards.
- Types: PCIe x16, PCIe x8, PCIe x4, PCIe x1, with x16 being commonly used for GPUs.
5. Storage Connectors
- SATA Ports: For connecting HDDs, SSDs, and optical drives.
- M.2 Slots: For high-speed SSDs and other expansion cards. Can support NVMe or SATA-based M.2 drives.
6. Power Connectors
- 24-pin ATX Connector: Main power supply connector for the motherboard.
- 8-pin (4+4) CPU Power Connector: Additional power supply for the CPU.
7. BIOS/UEFI Chip
- Description: Contains the system firmware that initializes hardware during boot and provides a setup utility for configuring hardware settings.
8. I/O Ports
- Description: Ports located on the back panel of the motherboard for connecting external devices.
- Examples: USB ports, Ethernet port, audio jacks, HDMI/DisplayPort, etc.
9. CMOS Battery
- Description: Battery that powers the CMOS chip to retain BIOS/UEFI settings and system clock when the computer is off.
10. Heat Sinks and Fan Headers
- Description: Areas for attaching cooling solutions. Fan headers are for connecting case and CPU fans.
11. Internal Connectors
- Description: Connectors for internal components like front panel buttons (power, reset), USB headers, and audio headers.
12. Memory Slots
- Description: Additional slots for expanding system memory.
13. Audio Chips
- Description: Integrated audio components that manage sound output and input.
14. Network Chips
- Description: Integrated network interface card (NIC) for Ethernet connectivity.
These components work together to make sure the motherboard functions correctly and connects all parts of your computer system.
Features of motherboard
1. Chipset
- Function: The chipset is a crucial component that manages communication between the CPU, RAM, storage devices, and peripheral devices. It essentially controls the data flow within the computer.
- Types: Modern motherboards often use a single chipset that combines the functions of the Northbridge and Southbridge found in older designs. The chipset determines features like support for overclocking, types of RAM, and number of PCIe lanes.
- Example: Intel Z-series and AMD X-series chipsets offer robust features for high-performance and overclocking.
2. Form Factor
- Function: The form factor defines the physical size and layout of the motherboard, which affects case compatibility and expansion options.
- Types:
- ATX: Standard size, supports multiple expansion slots and features.
- Micro-ATX: Smaller than ATX, but still offers several expansion options.
- Mini-ITX: Compact size, ideal for small cases but usually has fewer expansion slots.
- Impact: Larger form factors generally offer more features and expansion options but require larger cases.
3. CPU Compatibility
- Function: The CPU socket determines which processors can be installed on the motherboard.
- Socket Types:
- LGA (Land Grid Array): Used by Intel CPUs (e.g., LGA 1200).
- AM4: Used by AMD Ryzen CPUs.
- Impact: The socket type must match the CPU you plan to use. Chipsets also play a role in compatibility and features.
4. RAM Support
- Function: Determines the type, speed, and capacity of RAM that the motherboard can handle.
- Specifications:
- Type: DDR4, DDR5 (older types like DDR3 are less common now).
- Capacity: Maximum amount of RAM the motherboard supports (e.g., 64GB, 128GB).
- Speed: Measured in MHz, affects the performance of the RAM.
- Impact: More RAM and higher speeds can improve multitasking and performance in memory-intensive applications.
5. Expansion Slots
- Function: Allow the addition of various expansion cards to enhance the system’s capabilities.
- Types:
- PCIe x16: Typically used for GPUs.
- PCIe x8, x4, x1: Used for other expansion cards like network cards or sound cards.
- Impact: The number and type of slots influence the ability to upgrade or add components like GPUs, additional storage, or specialized hardware.
6. Storage Connectors
- Function: Connect storage devices like HDDs and SSDs to the motherboard.
- Types:
- SATA Ports: For traditional HDDs and SATA SSDs. Typically support up to 6Gbps speeds.
- M.2 Slots: For high-speed NVMe SSDs, which offer faster data transfer rates compared to SATA SSDs.
- Impact: More connectors and support for higher-speed interfaces like NVMe can improve storage performance and capacity.
7. I/O Ports
- Function: Provide interfaces for connecting external devices.
- Types:
- USB Ports: For peripherals like keyboards, mice, and external drives. Includes USB 2.0, 3.0, and 3.1.
- Audio Jacks: For speakers, headphones, and microphones.
- Video Outputs: HDMI, DisplayPort, and sometimes older types like VGA.
- Ethernet Port: For wired network connections.
- Impact: More and diverse I/O ports increase connectivity options for various devices and peripherals.
8. BIOS/UEFI Firmware
- Function: Provides the low-level interface between the hardware and the operating system. It initializes and tests hardware components during boot.
- Features:
- BIOS: Traditional firmware interface.
- UEFI: Modern interface with more features and a graphical user interface.
- Impact: Allows configuration of hardware settings, boot order, and system optimization.
9. Power Connectors
- Function: Supply power to the motherboard and connected components.
- Types:
- 24-pin ATX Connector: Main power connector for the motherboard.
- 8-pin (4+4) CPU Power Connector: Provides additional power to the CPU.
- Impact: Proper power supply is essential for stable operation and to support high-performance components.
10. Audio and Network Chips
- Function: Handle audio output/input and network connectivity.
- Types:
- Audio Chips: Integrated sound solutions for onboard audio.
- Network Chips: Integrated Ethernet controllers for wired connections.
- Impact: Higher-quality audio chips and faster network controllers can improve multimedia experiences and connectivity.
11. Cooling Solutions
- Function: Manage the temperature of the CPU and other components to ensure optimal performance.
- Types:
- Fan Headers: For connecting and controlling case and CPU fans.
- Heat Sinks: Passive cooling solutions that dissipate heat from critical components.
- Impact: Effective cooling is crucial for maintaining system stability, especially under heavy load or overclocking.
12. Internal Connectors
- Function: Connect internal components and peripherals to the motherboard.
- Types:
- Front Panel Connectors: For power buttons, reset buttons, and LED indicators.
- USB Headers: For connecting front panel USB ports.
- Audio Headers: For front panel audio ports.
- Impact: Proper internal connections ensure that all case features and peripherals function correctly.
13. Integrated Graphics
- Function: Built-in graphics processing for basic display functions without a discrete GPU.
- Impact: Useful for systems where high-end graphics are not needed, saving cost and power. Not all motherboards have integrated graphics.
14. Overclocking Features
- Function: Allow users to increase the performance of the CPU, RAM, and other components beyond their standard specifications.
- Features:
- BIOS/UEFI Settings: Options for adjusting clock speeds, voltages, and other parameters.
- Enhanced Cooling Solutions: Necessary for maintaining stability during overclocking.
- Impact: Overclocking can improve performance but requires careful tuning and cooling.
15. Connectivity Options
- Function: Provide additional connectivity features beyond basic requirements.
- Types:
- Wi-Fi: Integrated wireless networking capability.
- Bluetooth: For connecting wireless peripherals and devices.
- Impact: Enhances system connectivity and convenience by integrating wireless features.
16. Security Features
- Function: Enhance system security and data protection.
- Features:
- TPM (Trusted Platform Module): Hardware-based encryption for secure data storage.
- BIOS/UEFI Passwords: Protection against unauthorized access to firmware settings.
- Impact: Adds layers of security to protect against data theft and unauthorized changes.
These features collectively determine the motherboard’s capabilities, performance, and suitability for different types of computing tasks. Let me know if you need more information on any specific feature!
Software
Software refers to a collection of programs, data, and instructions that tell a computer or electronic device how to perform specific tasks. Unlike hardware, which consists of physical components, software is intangible and consists of lines of code that can be executed by the hardware.
Key Aspects of Software
- Programs: These are sets of instructions that perform specific tasks or operations. Examples include word processors (like Microsoft Word) and web browsers (like Google Chrome).
- Data: Information processed by software, such as files, databases, and configuration settings. Data can be user-generated or system-related.
- Instructions: Code written in programming languages that dictates how software should operate and interact with hardware and other software.
Types of Software
1. Operating System (OS)
- Description: The core software that manages hardware resources and provides a platform for running applications.
- Examples:
- Windows: Known for its user-friendly interface and wide application support.
- macOS: Designed for Apple computers with a focus on integration with Apple’s ecosystem.
- Linux: Open-source and highly customizable, used in various environments from desktops to servers.
2. Application Software
- Description: Programs designed to perform specific tasks for users. These are what people typically interact with directly.
- Types:
- Productivity Software: Includes word processors (e.g., Microsoft Word), spreadsheets (e.g., Excel), and presentation software (e.g., PowerPoint).
- Media Software: Includes video editors (e.g., Adobe Premiere Pro), photo editors (e.g., Adobe Photoshop), and media players (e.g., VLC Media Player).
- Web Browsers: Software for accessing the internet, such as Google Chrome, Mozilla Firefox, and Microsoft Edge.
- Games: Interactive entertainment software like Fortnite, Minecraft, and The Witcher series.
3. System Software
- Description: Software that supports the operation of hardware and provides a platform for running application software.
- Examples:
- Device Drivers: Small programs that allow the operating system to communicate with hardware components (e.g., printers, graphics cards).
- Utilities: Tools for system maintenance and optimization (e.g., disk cleanup, defragmentation tools).
4. Firmware
- Description: Specialized software embedded into hardware devices to control their functions. Firmware is often essential for the hardware’s basic operation.
- Examples:
- BIOS/UEFI: Firmware that initializes hardware during the boot process in computers.
- Router Firmware: Controls the functionality of networking hardware like routers and switches.
5. Development Software
- Description: Tools and environments used to create and maintain other software.
- Types:
- Integrated Development Environments (IDEs): Software applications that provide comprehensive facilities for software development (e.g., Visual Studio, Eclipse).
- Compilers and Interpreters: Tools that translate code written in high-level programming languages into machine code (e.g., GCC for C/C++, Python interpreter).
6. Security Software
- Description: Software designed to protect systems from various security threats.
- Examples:
- Antivirus Software: Protects against malware and viruses (e.g., Norton, McAfee).
- Firewalls: Monitors and controls incoming and outgoing network traffic (e.g., Windows Defender Firewall).
- Encryption Tools: Protects data by converting it into a secure format (e.g., BitLocker, VeraCrypt).
7. Utilities
- Description: Specialized tools designed to perform maintenance and system management tasks.
- Examples:
- Backup Software: Creates copies of data to prevent loss (e.g., Acronis True Image).
- System Monitoring Tools: Provides information about system performance and resource usage (e.g., CPU-Z, HWMonitor).
8. Network Software
- Description: Manages and facilitates network communication and connectivity.
- Examples:
- Network Operating Systems: Software designed for managing network resources (e.g., Windows Server, Cisco IOS).
- Network Management Tools: For monitoring and managing network performance (e.g., SolarWinds, Wireshark).
9. Business Software
- Description: Software tailored to specific business needs and processes.
- Examples:
- Enterprise Resource Planning (ERP): Integrates core business processes (e.g., SAP, Oracle ERP).
- Customer Relationship Management (CRM): Manages interactions with customers (e.g., Salesforce, HubSpot).
Each type of software serves a distinct purpose and contributes to the overall functionality of computing systems
BIOS
The BIOS (Basic Input/Output System) is a firmware component that initializes and tests the hardware components of a computer during the boot process and provides a low-level interface for the operating system to interact with the hardware. Here’s a detailed look at what BIOS is and its functions:
1. Definition and Purpose
- Definition: BIOS is a type of firmware that is embedded on a chip on the motherboard. It contains the essential code needed to start the computer and prepare the system hardware for use by the operating system.
- Purpose: To perform hardware initialization, provide an interface for system configuration, and facilitate the boot process.
2. Key Functions of BIOS
- Power-On Self-Test (POST): When the computer is powered on, BIOS performs POST to check the integrity and functionality of the hardware components such as the CPU, RAM, and storage devices.
- Hardware Initialization: BIOS initializes and configures system components such as the CPU, memory, storage devices, and peripherals to ensure they are ready for the operating system.
- Boot Process: After initializing the hardware, BIOS locates the boot device (such as a hard drive or USB drive) and loads the bootloader, which then loads the operating system.
- System Configuration: BIOS provides a setup utility (BIOS Setup or UEFI Firmware Settings) that allows users to configure hardware settings such as boot order, clock speeds, and power management.
- Interrupt Handling: BIOS manages hardware interrupts and communicates between the CPU and peripheral devices, facilitating efficient data transfer and device control.
Importance of Bios and functions of Bios
The BIOS (Basic Input/Output System) is a fundamental component in a computer’s architecture. It performs essential tasks during the boot process and provides critical functions for hardware interaction. Here’s a detailed look at its importance and functions:
Importance of BIOS
- Hardware Initialization
- Description: BIOS initializes and configures hardware components, ensuring they are ready for the operating system.
- Importance: Without proper initialization, hardware components like the CPU, RAM, and storage devices may not function correctly, leading to system instability or failure to boot.
- System Configuration
- Description: BIOS provides a setup utility for configuring hardware settings.
- Importance: Users can adjust settings such as boot order, clock speeds, and power management, which can optimize system performance and compatibility.
- Boot Process Management
- Description: BIOS locates and loads the bootloader from the designated boot device.
- Importance: This is crucial for starting the operating system and ensuring that the computer is able to load and run software.
- Hardware Abstraction
- Description: Provides a low-level interface between the operating system and hardware.
- Importance: Allows the operating system to interact with various hardware components through standardized interfaces, enabling consistent operation.
- System Security
- Description: BIOS can include security features such as password protection and secure boot.
- Importance: Enhances system security by preventing unauthorized access to BIOS settings and ensuring that only trusted software is loaded during boot.
Functions of BIOS
- Power-On Self-Test (POST)
- Function: Performs a diagnostic test of the system’s hardware components to ensure they are functioning correctly.
- Details: Checks components such as the CPU, RAM, and storage devices. If POST detects any issues, it may produce error messages or beep codes.
- Hardware Initialization
- Function: Configures and initializes system hardware to prepare it for use by the operating system.
- Details: Sets up the CPU, initializes RAM, detects and configures storage devices, and prepares other peripherals.
- Boot Process
- Function: Locates and loads the bootloader from the boot device.
- Details: BIOS checks the boot order defined in its settings to identify the device (e.g., hard drive, USB drive) containing the bootloader and transfers control to it.
- System Configuration
- Function: Provides a user interface for configuring various hardware settings.
- Details: Through the BIOS Setup Utility, users can adjust settings related to boot sequence, CPU and memory configurations, power management, and more.
- Interrupt Handling
- Function: Manages hardware interrupts to allow devices to communicate with the CPU.
- Details: Handles interrupt requests (IRQs) from hardware devices, ensuring timely and efficient processing of tasks.
- Firmware Updates
- Function: Allows the BIOS to be updated to add new features or fix issues.
- Details: Users can flash the BIOS with new firmware provided by the motherboard manufacturer to improve compatibility or performance.
- Legacy vs. UEFI
- Function: Provides a basic interface for booting and hardware interaction, with UEFI offering enhanced features.
- Details: UEFI replaces traditional BIOS with a more advanced interface, supporting larger drives, faster boot times, and improved security features.
- Security Features
- Function: Implements security measures to protect the system.
- Details: Includes options for setting BIOS passwords to prevent unauthorized access and features like Secure Boot to ensure only trusted software is loaded during the boot process.
Summary
- Importance: BIOS is crucial for initializing hardware, managing the boot process, configuring system settings, and providing a secure and stable environment for the operating system.
- Functions: Includes POST, hardware initialization, boot process management, system
What is BOOT
The term “BOOT” refers to the process of starting up a computer and loading the operating system from the storage device into the computer’s memory. The term originates from “bootstrap,” which metaphorically represents the process of lifting oneself up by one’s own bootstraps. Here’s a detailed explanation of the boot process:
1. Boot Process Overview
- Power-On:
- When you power on your computer, the power supply sends power to the motherboard and other components.
- POST (Power-On Self-Test):
- Function: The BIOS performs POST to check and initialize the hardware components, such as the CPU, RAM, and storage devices.
- Details: It ensures that all critical hardware components are functioning correctly. If there are issues, the BIOS may produce error messages or beep codes.
- BIOS/UEFI Initialization:
- Function: The BIOS or UEFI firmware takes control after POST to configure hardware settings and prepare the system for the operating system.
- Details: It initializes and configures system components, such as CPU, memory, and storage devices. UEFI provides more advanced features compared to traditional BIOS.
- Boot Device Detection:
- Function: BIOS/UEFI determines the boot device from which the operating system will be loaded.
- Details: The boot order is defined in the BIOS/UEFI settings, specifying which devices (e.g., hard drive, USB drive, CD/DVD) to check for a bootable operating system.
- Loading the Bootloader:
- Function: BIOS/UEFI locates and loads the bootloader from the designated boot device.
- Details: The bootloader is a small program responsible for loading the operating system. Examples include GRUB (for Linux) and Windows Boot Manager.
- Operating System Loading:
- Function: The bootloader transfers control to the operating system.
- Details: The operating system’s kernel is loaded into memory, and the system begins to initialize drivers and system services.
- System Initialization:
- Function: The operating system completes its startup process, initializes system services, and prepares the system for user interaction.
- Details: This includes starting background processes, initializing user interfaces, and loading system settings.
2. Key Components of the Boot Process
- Power Supply:
- Provides power to the motherboard and other components.
- BIOS/UEFI Firmware:
- Manages the initial hardware configuration and boot process.
- POST:
- Tests and initializes hardware components.
- Boot Device:
- The storage device (e.g., hard drive, SSD, USB drive) from which the operating system is loaded.
- Bootloader:
- A small program that loads the operating system. Examples include GRUB, LILO, and Windows Boot Manager.
- Operating System Kernel:
- The core part of the operating system that manages hardware and system resources.
3. Types of Boot Processes
- Cold Boot (Hard Boot):
- Occurs when the computer is powered on from a completely off state.
- Involves a full initialization of hardware and the boot process.
- Warm Boot (Soft Boot):
- Occurs when the computer is restarted without turning off the power.
- Usually involves a reboot process where the BIOS/UEFI is reloaded but hardware initialization is minimal compared to a cold boot.
4. Troubleshooting Boot Issues
- Error Messages: BIOS/UEFI or operating system error messages can indicate hardware or software issues.
- Boot Device Issues: Problems with the boot device (e.g., corrupted files, failed drive) can prevent the operating system from loading.
- Hardware Failures: Faulty hardware components can disrupt the boot process and require diagnostics or replacement.
Summary
The boot process is essential for starting a computer and loading the operating system. It involves powering on the system, performing POST, initializing hardware, detecting the boot device, loading the bootloader, and finally loading and initializing the operating system. Each step is crucial for ensuring that the computer is ready for user interaction and application use.
Post and importance BEEP codes
POST (Power-On Self-Test)
POST is a diagnostic process performed by the BIOS (Basic Input/Output System) when a computer is powered on. It checks the hardware components to ensure they are functioning correctly before handing over control to the operating system. The POST sequence is essential for the system’s stability and successful booting.
Importance of POST
- System Stability:
- Ensures: Verifies that essential hardware components are functioning correctly, which is crucial for system stability and performance.
- Early Error Detection:
- Identification: Identifies hardware issues early in the boot process, allowing users or technicians to address problems before the operating system starts.
- Hardware Initialization:
- Prepares: Initializes and configures hardware components to ensure they are ready for use by the operating system.
- Error Indication:
- Alerts: Provides diagnostic information through beep codes or error messages to help troubleshoot hardware issues.
Beep Codes
Beep Codes are audible signals generated by the computer’s motherboard during POST to indicate hardware issues. Different beep patterns correspond to specific errors, and they vary between different motherboard manufacturers.
Understanding Beep Codes
- Single Beep:
- Meaning: Typically indicates that the system has passed POST and is proceeding with booting.
- Exceptions: The interpretation can vary based on the motherboard’s BIOS or UEFI.
- Multiple Beeps:
- Meaning: Multiple beeps can signify various hardware issues depending on the pattern. For example:
- 1 Short Beep: System is functioning correctly (general indication).
- 1 Long Beep, 2 Short Beeps: Indicates a problem with the video card (common in older systems).
- Continuous Beeping: Often suggests a memory error or a hardware issue requiring immediate attention.
- Meaning: Multiple beeps can signify various hardware issues depending on the pattern. For example:
- Beep Code Patterns:
- AMI BIOS: May use patterns such as 1-3-3-1 to indicate specific issues like a memory problem.
- Award BIOS: May use patterns like 1-2-3 to indicate problems with the video card or memory.
- Consulting Documentation:
- Motherboard Manual: For accurate beep code interpretation, refer to the motherboard’s manual or manufacturer’s website. Beep codes can vary between different BIOS versions and motherboard manufacturers.
Examples of Common Beep Codes
- Phoenix BIOS:
- 1-1-3 Beep Code: Indicates a problem with the motherboard or a memory issue.
- 2-1-1 Beep Code: Suggests an issue with the video card.
- AMI BIOS:
- 1 Beep: Indicates a successful POST.
- 3 Beeps: Often indicates a memory problem.
- Award BIOS:
- 1 Long, 2 Short Beeps: Indicates a problem with the video card.
Summary
- POST: The Power-On Self-Test is a crucial diagnostic process that ensures hardware components are functioning correctly before the operating system starts.
- Importance: It helps in detecting hardware issues early, initializes hardware components, and prepares the system for booting.
- Beep Codes: Provide audible signals indicating hardware issues during POST. Different beep patterns correspond to specific errors, and interpreting these codes helps in troubleshooting hardware problems.
POST and beep codes are vital for ensuring that a computer system is stable and operational, helping users and technicians diagnose and resolve hardware issues effectively.
Different Connectors
- Power Connectors: Supply power to components (e.g., ATX, CPU, SATA power).
- Data Connectors: Transfer data between components (e.g., SATA, PCIe, M.2).
- Input/Output Connectors: Connect peripherals and displays (e.g., USB, HDMI, DisplayPort).
- Audio Connectors: Manage audio input and output (e.g., 3.5mm jack, Optical Audio).
- Network Connectors: Facilitate network connections (e.g., RJ-45, RJ-11).
- Peripheral Connectors: Connect older peripherals (e.g., PS/2).
- Internal Connectors: Connect internal components (e.g., front panel headers).
- Specialized Connectors: Serve specific purposes (e.g., eSATA, docking connectors).
These connectors play a crucial role in ensuring that all components and peripherals in a computer system can communicate effectively and perform their intended functions.

Meaning of Computer networking
Computer networking refers to the practice of connecting multiple computers and other devices to share resources and information. It involves the design, implementation, and management of networks to enable communication and data exchange between devices. Here’s a comprehensive overview:
1. Definition and Purpose
- Definition: Computer networking is the process of linking computers, servers, mainframes, network devices, and other devices to share data and resources. This can be achieved through physical cables, wireless connections, or a combination of both.
- Purpose: To enable communication between devices, facilitate data sharing, access to resources, and provide services such as email, file sharing, and internet access.
2. Types of Networks
- Local Area Network (LAN):
- Scope: Covers a small geographical area like a home, office, or building.
- Components: Includes computers, printers, servers, and network devices connected via Ethernet cables or Wi-Fi.
- Example: An office network where all employees’ computers are connected to a central server.
- Wide Area Network (WAN):
- Scope: Covers a large geographical area, often connecting multiple LANs across cities, countries, or continents.
- Components: Includes various types of networking devices and connections, such as leased lines and satellite links.
- Example: The internet, which connects millions of networks worldwide.
- Metropolitan Area Network (MAN):
- Scope: Covers a city or large campus.
- Components: Connects multiple LANs within a metropolitan area.
- Example: A university network spanning multiple buildings within a city.
- Personal Area Network (PAN):
- Scope: Covers a very small area, typically within a few meters.
- Components: Includes devices like smartphones, tablets, and laptops connected via Bluetooth or USB.
- Example: A network connecting a smartphone to a laptop via Bluetooth.
- Virtual Private Network (VPN):
- Scope: Provides a secure, encrypted connection over a public network (like the internet) to a private network.
- Components: Uses VPN protocols to create a secure tunnel for data.
- Example: Remote workers accessing their company’s internal network securely from home.
3. Network Topologies
- Bus Topology: All devices are connected to a single central cable. Data travels in both directions along the bus.
- Star Topology: All devices are connected to a central hub or switch. Data is sent to the hub, which then directs it to the appropriate device.
- Ring Topology: Devices are connected in a circular fashion. Data travels in one or both directions around the ring.
- Mesh Topology: Devices are interconnected, allowing multiple paths for data to travel. Can be fully meshed or partially meshed.
- Tree Topology: A hybrid of star and bus topologies. Groups of star-configured networks are connected to a central bus.
4. Networking Devices
- Router: Connects different networks and directs data between them. It also manages traffic within a network.
- Switch: Connects devices within a LAN and directs data to specific devices based on MAC addresses.
- Hub: A basic networking device that connects multiple devices in a LAN but does not manage traffic efficiently.
- Modem: Converts digital data from a computer into analog signals for transmission over phone lines and vice versa.
- Access Point: Provides wireless connectivity to devices within a network, typically used in Wi-Fi networks.
- Firewall: Monitors and controls incoming and outgoing network traffic based on predetermined security rules.
5. Networking Protocols
- TCP/IP (Transmission Control Protocol/Internet Protocol): The fundamental suite of protocols used for communication over the internet and most networks. It includes IP for addressing and TCP for reliable data transmission.
- HTTP/HTTPS (Hypertext Transfer Protocol/Secure): Used for transferring web pages and data over the internet. HTTPS includes encryption for security.
- FTP (File Transfer Protocol): Used for transferring files between devices on a network.
- SMTP (Simple Mail Transfer Protocol): Used for sending email between servers.
- DNS (Domain Name System): Translates domain names into IP addresses.
**6. Network Security
- Encryption: Protects data by converting it into a secure format that can only be read by authorized parties.
- Authentication: Ensures that users or devices accessing the network are who they claim to be.
- Firewalls: Filter and control network traffic to protect against unauthorized access and attacks.
- Anti-Virus Software: Detects and removes malicious software from networked devices.
Summary
Computer networking is a crucial aspect of modern computing that connects multiple devices and systems to facilitate communication, data sharing, and resource management. It involves various network types, topologies, devices, protocols, and security measures to ensure efficient and secure network operations. Networking enables everything from local file sharing to global internet access and supports a wide range of applications and services.
Difference between IAN,WAN,MAN
| Aspect | LAN (Local Area Network) | WAN (Wide Area Network) | MAN (Metropolitan Area Network) |
|---|---|---|---|
| Geographical Coverage | Small area such as a home, office, or building | Large geographical area such as cities, countries, or continents | Medium geographical area such as a city or large campus |
| Typical Use Case | Connecting devices within a single location (e.g., office network) | Connecting multiple LANs across larger distances (e.g., the internet) | Connecting multiple LANs within a metropolitan area (e.g., city-wide network) |
| Network Speed | Generally high speed, ranging from 10 Mbps to 10 Gbps or more | Varies widely, can be slower compared to LANs due to distance and routing | Moderate to high speed, typically between LAN and WAN speeds |
| Hardware | Network switches, routers, hubs, and network cables (Ethernet) | Routers, switches, leased lines, satellites, fiber optics | Routers, switches, fiber optics, and leased lines |
| Setup Complexity | Relatively simple setup and configuration | Complex setup due to large scale and diverse technologies | Moderate complexity, typically involves more advanced networking equipment |
| Cost | Generally low cost for setup and maintenance | High cost due to extensive infrastructure and technology | Moderate cost, higher than LAN but generally lower than WAN |
| Data Transmission | Typically uses Ethernet cables or Wi-Fi | Uses various technologies including fiber optics, satellites, and leased lines | Uses fiber optics, leased lines, and sometimes wireless technologies |
| Examples | Home network, office network | The internet, corporate networks spanning multiple cities | University networks, city-wide Wi-Fi networks |
| Security | Generally secure within a controlled environment | Requires robust security measures due to exposure to wider networks | Security measures are needed but usually less complex than WANs |
| Maintenance | Easier to manage and maintain due to smaller scale | Requires ongoing maintenance and monitoring due to complexity and scale | Requires regular maintenance, typically managed by service providers |
Summary
- LAN (Local Area Network): Ideal for connecting devices within a small, localized area, offering high speeds and relatively low costs. It’s used for personal or organizational networks within a single building or campus.
- WAN (Wide Area Network): Spans large geographical distances, connecting multiple LANs and other networks. It is more complex and expensive, often involving various types of technology and infrastructure.
- MAN (Metropolitan Area Network): Covers a city or large campus, bridging the gap between LANs and WANs. It provides moderate to high-speed connectivity over a medium-sized area and is often used for city-wide or large institutional networks.
Difference Between Internet and Intranet
- Internet: The Internet is a global network providing access to a vast range of public resources and services. It is accessible from anywhere with an internet connection and is managed by various entities worldwide. It offers broad access to information but requires strong security measures to protect against various online threats.
- Intranet: An Intranet is a private network restricted to a specific organization or group. It provides secure access to internal resources and communication tools. It is used to share information and collaborate within the organization and is protected from external access through various security measures.
| Aspect | Internet | Intranet |
|---|---|---|
| Definition | A global network connecting millions of private, public, academic, business, and government networks | A private network used within an organization to share information and resources securely |
| Scope | Worldwide; accessible from anywhere with an internet connection | Restricted to a specific organization or group, accessible only from within the organization or through secured access |
| Accessibility | Publicly accessible; requires an internet connection | Privately accessible; requires authentication and authorization to access |
| Security | Less secure; susceptible to various online threats and attacks, requires robust security measures | More secure within its boundaries; managed by the organization, often protected by firewalls and other security measures |
| Usage | Used for browsing websites, emailing, social networking, accessing various online services and resources | Used for internal communication, sharing documents, collaborating on projects, and managing internal resources |
| Network Type | A network of networks that connects millions of individual networks globally | A local or wide area network within an organization, isolated from the public internet |
| Content | Contains a vast array of publicly available content, including websites, services, and databases | Contains internal documents, applications, and resources exclusive to the organization |
| Administration | Managed by various ISPs, governments, and organizations globally | Managed by the organization’s IT department or network administrators |
| Examples | Websites like Google, Facebook, Wikipedia, etc. | Company’s internal portal, employee intranet site, internal communication tools like Slack or SharePoint |
| Cost | Generally free to use but may involve costs for certain services or content | Typically involves costs related to setup, maintenance, and security but usually managed within the organization’s budget |
Summary
While both the Internet and Intranet are essential for modern communication and information sharing, they serve different purposes and operate under different access and security conditions.
Internet service provider
An Internet Service Provider (ISP) is a company or organization that provides individuals, businesses, and other entities with access to the Internet. ISPs offer a variety of services and play a critical role in enabling connectivity and data transmission. Here’s a detailed overview of ISPs:
1. Role and Function
- Connectivity: ISPs provide the necessary infrastructure and technology to connect users to the Internet. This includes managing and maintaining network connections, routing data, and ensuring connectivity.
- Bandwidth: They offer different bandwidth options, which determine the speed and capacity of the Internet connection.
- Support: ISPs often provide customer support for troubleshooting and resolving connectivity issues.
2. Types of ISPs
- Dial-Up ISP:
- Technology: Uses a telephone line to connect to the Internet.
- Speed: Generally slow, with speeds up to 56 kbps.
- Usage: Less common today, mostly replaced by faster broadband technologies.
- Broadband ISP:
- Types: Includes several technologies:
- DSL (Digital Subscriber Line): Uses telephone lines but offers higher speeds than dial-up.
- Cable: Uses cable television lines to provide high-speed Internet access.
- Fiber Optic: Uses fiber-optic cables to provide very high-speed Internet connections.
- Satellite: Provides Internet access via satellite signals, useful in remote areas but can have higher latency.
- Fixed Wireless: Provides Internet access using radio signals, typically to rural or underserved areas.
- Speed: Generally fast, ranging from a few Mbps to several Gbps.
- Types: Includes several technologies:
- Cellular ISP:
- Technology: Provides Internet access via mobile networks (3G, 4G, 5G).
- Speed: Varies by network generation and signal strength; 4G and 5G offer high-speed options.
- Usage: Often used for mobile devices and as a backup or secondary Internet source.
- Satellite ISP:
- Technology: Provides Internet access via satellite communication.
- Speed: Varies but can be slower than terrestrial broadband due to latency.
- Usage: Ideal for remote or rural areas where other types of connectivity are unavailable.
3. Services Provided by ISPs
- Internet Access: Basic connectivity to the Internet.
- Email Hosting: Providing email accounts and services.
- Web Hosting: Offering space on a server for hosting websites.
- Domain Registration: Assisting with registering and managing domain names.
- Technical Support: Helping with connectivity issues, troubleshooting, and customer service.
4. Common ISP Terms
- Bandwidth: The maximum rate at which data can be transmitted over an Internet connection. Higher bandwidth allows for faster data transfer and better performance.
- Data Cap: A limit on the amount of data that can be used during a billing cycle. Exceeding this cap can result in extra charges or reduced speeds.
- Latency: The time it takes for data to travel from the source to the destination. Lower latency is better for real-time applications like gaming and video calls.
5. Choosing an ISP
When selecting an ISP, consider the following factors:
- Speed: Choose an ISP that offers speeds that meet your needs for streaming, gaming, or work.
- Availability: Not all ISPs are available in every geographic area. Check which ISPs serve your location.
- Cost: Compare pricing plans, including any installation fees, monthly charges, and data caps.
- Reliability: Look for an ISP with a good reputation for uptime and customer service.
- Customer Support: Ensure the ISP provides responsive and helpful customer support.
Summary
An Internet Service Provider (ISP) is crucial for delivering Internet connectivity to individuals and businesses. They offer various types of services, including dial-up, broadband, cellular, and satellite Internet. Choosing the right ISP involves considering factors like speed, cost, availability, and support to ensure a reliable and effective Internet experience.
Role of modem in Accessing the Internet
A modem (short for modulator-demodulator) plays a crucial role in accessing the Internet by facilitating the communication between your computer or network and your Internet Service Provider (ISP). Here’s a detailed explanation of the modem’s role:
1. Function of a Modem
- Modulation and Demodulation:
- Modulation: Converts digital signals from your computer into analog signals that can be transmitted over telephone lines, cable systems, or satellite links.
- Demodulation: Converts incoming analog signals from the ISP into digital signals that your computer or network can understand.
- Data Transmission:
- Transmit Data: Sends data from your computer to the ISP through the communication medium (e.g., phone line, coaxial cable, fiber optics).
- Receive Data: Receives data from the ISP and converts it into a format that can be used by your computer or network.
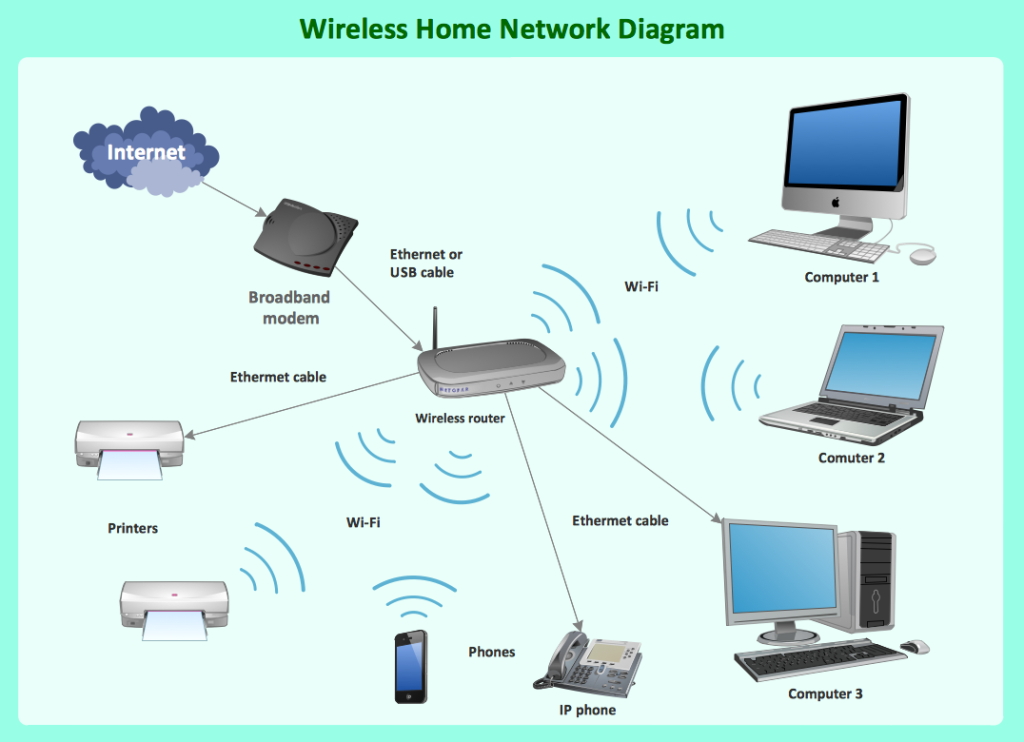
Internet security
Internet security refers to the practices, technologies, and measures designed to protect data and systems from threats and unauthorized access while using the Internet. It encompasses a range of strategies and tools aimed at safeguarding sensitive information, maintaining privacy, and ensuring the integrity and availability of online services. Here’s a comprehensive overview of internet security:
1. Key Components of Internet Security
- Encryption:
- Purpose: Protects data by converting it into an unreadable format that can only be deciphered with a key.
- Types:
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): Used for securing data transmitted over the web (e.g., HTTPS).
- AES (Advanced Encryption Standard): A widely used encryption algorithm for securing data at rest and in transit.
- Authentication:
- Purpose: Ensures that users or systems are who they claim to be.
- Methods:
- Passwords: Basic authentication method; should be strong and unique.
- Two-Factor Authentication (2FA): Adds an additional layer of security by requiring two forms of identification (e.g., password and SMS code).
- Biometrics: Uses physical characteristics like fingerprints or facial recognition.
- Firewalls:
- Purpose: Monitors and controls incoming and outgoing network traffic based on security rules.
- Types:
- Hardware Firewalls: Physical devices that protect networks.
- Software Firewalls: Installed on individual devices to monitor traffic.
- Anti-Virus and Anti-Malware Software:
- Purpose: Detects, prevents, and removes malicious software like viruses, worms, and trojans.
- Features: Real-time scanning, malware removal, and threat detection.
- Intrusion Detection and Prevention Systems (IDPS):
- Purpose: Monitors network or system activities for malicious activities or policy violations and takes action to prevent them.
- Types:
- Intrusion Detection Systems (IDS): Detects and alerts about potential threats.
- Intrusion Prevention Systems (IPS): Detects and takes action to block or prevent threats.
- Secure Sockets Layer (SSL)/Transport Layer Security (TLS):
- Purpose: Provides a secure connection between a web server and a browser, ensuring that data transferred over the web is encrypted and secure.
- Usage: Indicated by HTTPS in web addresses and a padlock symbol in browsers.
- Virtual Private Network (VPN):
- Purpose: Creates a secure, encrypted connection over a public network (e.g., the Internet) to protect data and privacy.
- Usage: Used for secure remote access and to mask IP addresses.
- Data Backup and Recovery:
- Purpose: Ensures that data is regularly backed up and can be restored in case of loss or corruption.
- Methods: Cloud backups, external drives, and regular data snapshots.
