Introduction of Communication Technologies
Communication technologies encompass a broad range of systems and methods used to convey information from one place to another. These technologies enable different forms of interaction, including voice, text, video, and data transfer. Here’s an introduction to some of the key communication technologies and concepts:
1. Types of Communication Technologies
a. Wired Communication
- Telephone Networks: Traditional landline systems that use analog or digital signals to transmit voice.
- Fiber Optic Communication: Uses light signals transmitted through optical fibers to achieve high-speed and high-bandwidth data transfer.
- Ethernet: A common LAN technology that uses wired connections to transmit data in a network.
b. Wireless Communication
- Cellular Networks: Includes technologies like 2G, 3G, 4G, and 5G, providing voice and data services over wireless networks using cell towers.
- Wi-Fi: Wireless technology used for local area networking based on the IEEE 802.11 standards, commonly used in homes and businesses.
- Bluetooth: Short-range wireless technology for communication between devices, such as headsets, keyboards, and smartphones.
c. Satellite Communication
- Geostationary Satellites: Satellites positioned in a fixed orbit above the Earth, used for TV broadcasting, weather monitoring, and global communications.
- Low Earth Orbit (LEO) Satellites: Satellites in lower orbits used for internet access and global communication, including systems like Starlink.
d. Internet-Based Communication
- Email: A system for sending and receiving messages electronically over the internet.
- Instant Messaging (IM): Real-time text communication between users, often using protocols like XMPP or applications like WhatsApp and Telegram.
- VoIP (Voice over Internet Protocol): Technology for delivering voice communications over the internet, with services like Skype and Zoom.
IEEE 802.15.4
IEEE 802.15.4 is a standard developed by the Institute of Electrical and Electronics Engineers (IEEE) for low-rate wireless personal area networks (LR-WPANs). It is specifically designed for devices with limited processing capabilities and constrained power sources, making it ideal for applications in the Internet of Things (IoT) and other wireless sensor networks. Here are the key features of IEEE 802.15.4:
1. Low Power Consumption
- Energy Efficiency: Designed for devices that need to operate for long periods on small batteries. It employs power-saving techniques like sleep modes to minimize energy usage.
- Duty Cycling: Devices can remain in a low-power sleep mode most of the time and wake up only to transmit or receive data.
2. Low Data Rates
- Data Rate Options: Provides several data rate options to balance power consumption and communication needs:
- 250 kbps in the 2.4 GHz ISM band
- 40 kbps in the 915 MHz ISM band
- 20 kbps in the 868 MHz ISM band
3. Short Range
- Communication Range: Typically supports communication over short distances, ranging from 10 to 100 meters, depending on the environment and radio power settings.
- Applications: Suitable for use in confined areas like homes, buildings, or within a specific industrial site.
4. Simple Protocol
- Minimal Overhead: The protocol has a simple, lightweight design with minimal header and control information, which contributes to low power consumption.
- Low Complexity: The protocol stack is designed to be simple to implement, reducing the processing and memory requirements of devices.
5. Network Topologies
- Star Topology: Devices communicate through a central coordinator, which manages the network and handles communications between devices.
- Peer-to-Peer (Mesh) Topology: Devices communicate directly with each other, enabling more robust and flexible network configurations. This allows for data to be relayed through intermediate nodes to extend coverage and improve reliability.
IEEE 802.15.4 Variants
The IEEE 802.15.4 standard has several variants that cater to different frequency bands, data rates, and application needs. These variants are designed to optimize performance based on specific requirements, such as range, power consumption, and data throughput. Here are the key variants of IEEE 802.15.4:
1. IEEE 802.15.4-2003
- Frequency Bands: Operates in the 868 MHz band (Europe) and 915 MHz band (North America).
- Data Rates: Provides data rates of 20 kbps (868 MHz) and 40 kbps (915 MHz).
- Applications: Targeted at early low-power wireless sensor networks and home automation.
2. IEEE 802.15.4-2006
- Frequency Bands: Introduces the 2.4 GHz ISM band, in addition to the existing 868 MHz and 915 MHz bands.
- Data Rates: Adds a data rate of 250 kbps for the 2.4 GHz band.
- Applications: Expanded to support more applications and regions, including global deployments.
3. IEEE 802.15.4-2011
- Frequency Bands: Continues to use the 2.4 GHz, 915 MHz, and 868 MHz bands.
- Data Rates: Maintains existing data rates (20 kbps, 40 kbps, and 250 kbps).
- Enhancements: Includes enhancements to improve network performance, such as better support for mesh networking and improved security features.
4. IEEE 802.15.4-2015
- Frequency Bands: Uses the 2.4 GHz, 915 MHz, and 868 MHz bands.
- Data Rates: Maintains existing data rates but introduces improvements for mesh networking.
- Enhancements: Focuses on additional features to support low-power, low-data-rate communication, and integration with other standards like Zigbee and Thread.
5. IEEE 802.15.4-2020
- Frequency Bands: Expands to include new frequency bands for improved global usability, including support for sub-GHz frequencies like 433 MHz and additional bands in the 1 GHz range.
- Data Rates: Maintains the traditional data rates but introduces enhancements for better support of modern applications.
- Enhancements: Includes advancements for low-latency communication, improved security, and better performance in challenging environments. It also enhances support for more robust mesh networking and coexistence with other wireless technologies.
Key Variants by Frequency Band
- 2.4 GHz Band:
- Standard: IEEE 802.15.4-2006 and later.
- Data Rate: 250 kbps.
- Applications: Widely used globally; supports a wide range of applications, including consumer electronics, smart home devices, and IoT.
- 915 MHz Band:
- Standard: IEEE 802.15.4-2003 and later.
- Data Rate: 40 kbps.
- Applications: Primarily used in North America; suitable for industrial and outdoor applications.
- 868 MHz Band:
- Standard: IEEE 802.15.4-2003 and later.
- Data Rate: 20 kbps.
- Applications: Used in Europe; supports various low-power applications, including industrial and smart city deployments.
- Sub-GHz Bands:
- Standard: IEEE 802.15.4-2020.
- Data Rate: Varies by band.
- Applications: Supports more applications in different regions and environments, providing better range and penetration through obstacles.
Applications and Interoperability
- Zigbee: Often built on top of IEEE 802.15.4, adding a higher-level application framework for mesh networking, home automation, and industrial control.
- Thread: Also based on IEEE 802.15.4, Thread focuses on providing a robust mesh networking protocol for smart home and IoT applications.
- 6LoWPAN: Uses IEEE 802.15.4 for the physical and MAC layers, with additional protocol layers to enable IPv6 communication over low-power wireless networks.
These variants of IEEE 802.15.4 allow for flexibility in designing wireless communication systems to meet various needs and regulatory requirements, making it a versatile and widely used standard in the field of low-power wireless networks.
IEEE 802.15.4 TYPES
IEEE 802.15.4, the terms RFD (Reduced Function Device) and FFD (Full Function Device) refer to two types of device roles that define the capabilities and functionalities of devices within an IEEE 802.15.4 network. Here’s an overview of each:
1. Reduced Function Device (RFD)
- Definition: RFDs are devices with limited functionality, typically designed to be simpler and less resource-intensive. They are optimized for low-power operation and typically have minimal processing and memory resources.
- Features:
- Limited Capabilities: RFDs can perform basic communication functions but lack the full range of network management capabilities.
- Role: Usually act as end devices in the network. They communicate with FFDs but do not perform network management functions or routing.
- Network Participation: Can only communicate with FFDs and do not participate in network coordination or management.
- Power Efficiency: Designed to be energy-efficient, making them suitable for battery-operated or low-power applications.
- Use Cases:
- Simple Sensors: Devices like temperature or humidity sensors that only need to transmit data.
- Basic Actuators: Devices that perform simple actions based on commands from FFDs.
2. Full Function Device (FFD)
- Definition: FFDs are devices with comprehensive functionality, capable of performing all the tasks needed to manage and maintain the network. They have more processing power and memory compared to RFDs.
- Features:
- Full Capabilities: FFDs can act as coordinators, routers, or end devices. They can handle network management tasks, routing, and data processing.
- Role: Can operate in various roles, including as coordinators (network managers), routers (for extending network range and routing messages), or end devices (similar to RFDs but with additional capabilities).
- Network Participation: FFDs can communicate with both RFDs and other FFDs. They can manage network formation, address assignment, and data routing.
- Power Consumption: Generally consume more power than RFDs due to their increased functionality.
- Use Cases:
- Network Coordinators: Devices that manage the network, handle address allocation, and coordinate communication between devices.
- Routers: Devices that relay messages between RFDs and coordinators, extending the network’s range and ensuring data reaches its destination.
- Advanced Sensors: Devices with more processing capabilities that can handle complex tasks or multiple functions.
Summary
- RFD (Reduced Function Device):
- Simpler, lower-power devices.
- Limited to basic communication functions.
- Communicates with FFDs but not involved in network management.
- FFD (Full Function Device):
- More capable and resource-intensive devices.
- Can manage network functions, routing, and coordination.
- Can communicate with both RFDs and other FFDs.
These roles help define the structure and functionality of IEEE 802.15.4 networks, ensuring that devices can be appropriately designed and deployed based on their required capabilities and roles in the network.
What is ZIGBEE
Zigbee is a specification for a suite of high-level communication protocols used to create personal area networks (PANs) based on the IEEE 802.15.4 standard. It is designed for low-power, low-data-rate applications, and is particularly well-suited for use in scenarios requiring wireless communication between devices in a network with a relatively short range. Here’s an overview of Zigbee:
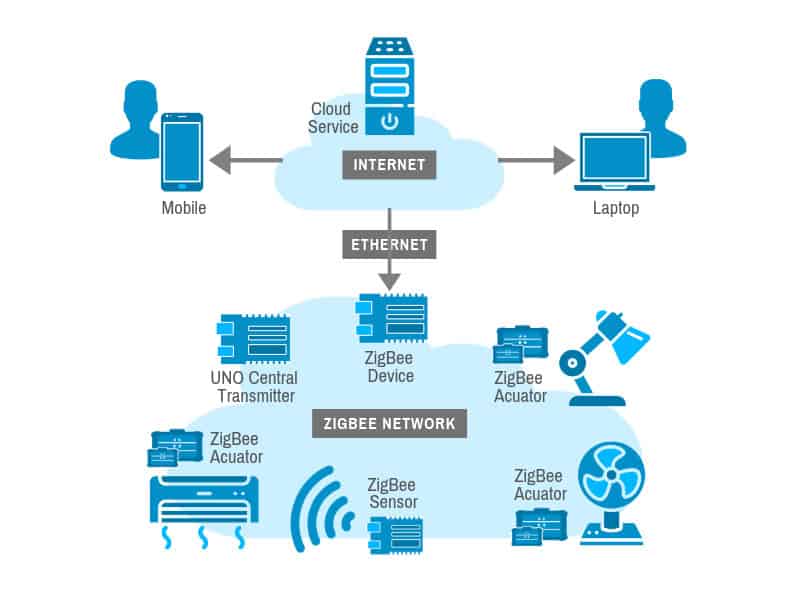
Key Features of Zigbee
- Low Power Consumption
- Energy Efficiency: Zigbee is optimized for low power consumption, allowing devices to operate for extended periods on small batteries.
- Sleep Modes: Devices can enter sleep modes to conserve energy when not actively communicating.
- Low Data Rate
- Data Rate: Typically supports data rates of up to 250 kbps, which is sufficient for most sensor and control applications.
- Application: Suitable for applications that do not require high-speed data transfer.
- Short Range
- Range: Zigbee devices typically communicate over distances ranging from 10 to 100 meters, depending on environmental conditions and radio power settings.
- Applications: Ideal for use in homes, buildings, and small outdoor areas.
- Mesh Networking
- Topology: Supports mesh networking, where devices can communicate with each other and relay messages through intermediate nodes to extend network coverage and improve reliability.
- Scalability: Allows for the creation of large networks with many devices, as nodes can cooperate to forward data and extend network range.
- Interoperability
- Standardization: Zigbee is based on the IEEE 802.15.4 standard for the PHY and MAC layers, and its higher-level protocol ensures interoperability among devices from different manufacturers.
- Application Profiles: Includes various application profiles for specific use cases, such as home automation, industrial control, and smart energy.
- Security
- Encryption: Supports AES-128 (Advanced Encryption Standard with a 128-bit key) for data encryption, ensuring secure communication.
- Authentication: Provides mechanisms for secure device authentication and data integrity.
- Flexibility and Reliability
- Device Roles: Devices in a Zigbee network can act as coordinators, routers, or end devices, depending on their capabilities and functions.
- Robust Communication: The mesh networking capability and collision avoidance mechanisms improve the reliability and robustness of the communication.
Zigbee Network Components
- Coordinator
- Role: Manages the network by handling device addressing, network formation, and synchronization.
- Function: Responsible for network initiation and maintaining the overall network structure.
- Router
- Role: Extends network range by routing messages between devices.
- Function: Can also act as an intermediary to forward data from end devices to coordinators or other routers.
- End Device
- Role: Communicates with coordinators or routers to send or receive data.
- Function: Typically has limited functionality and power requirements compared to routers and coordinators.
Applications of Zigbee
- Home Automation: Used for smart home devices such as lighting control, thermostats, door locks, and security systems.
- Industrial Control: Applied in industrial settings for monitoring and controlling equipment, asset tracking, and environmental sensing.
- Smart Energy: Utilized in smart meters, energy management systems, and demand response applications.
- Healthcare: Employed in remote patient monitoring, medical device management, and home health monitoring.
Overall, Zigbee is a versatile and efficient protocol for creating low-power, wireless networks, making it an important technology in the IoT and smart device ecosystem.
Different Topologies of ZIGBEE
Zigbee networks can be configured in different topologies, each with its own advantages and use cases. These topologies define how devices communicate within the network and impact factors like network range, reliability, and scalability. The main Zigbee topologies are:
1. Star Topology
- Description: In a star topology, all devices (end devices) communicate directly with a central coordinator.
- Coordinator: Manages the network, handles addressing, and controls communication between devices.
- End Devices: Communicate only with the coordinator and do not directly interact with other end devices.
- Advantages:
- Simplicity: Easy to set up and manage.
- Low Latency: Communication between devices and the coordinator is direct, leading to lower latency.
- Disadvantages:
- Single Point of Failure: If the coordinator fails, the entire network is affected.
- Limited Range: The range is limited to the reach of the coordinator, and devices cannot communicate beyond this range.

2. Mesh Topology
- Description: In a mesh topology, devices communicate with each other, and data can be relayed through multiple nodes to reach its destination. This topology allows devices to act as routers, forwarding data from other devices.
- Coordinator: Initiates the network and manages addressing. Can also act as a router or end device.
- Routers: Extend network range and improve communication reliability by forwarding messages between devices.
- End Devices: Can communicate with routers and coordinators, but not with other end devices directly.
- Advantages:
- Extended Range: Allows for larger networks as data can be relayed through multiple nodes.
- Improved Reliability: Provides redundancy and alternative communication paths, enhancing network robustness.
- Scalability: Supports a large number of devices.
- Disadvantages:
- Complexity: More complex to set up and manage compared to star topology.
- Increased Power Consumption: Routers consume more power as they forward messages, which can affect battery life in battery-operated devices.

3. Cluster Tree Topology
- Description: A variation of the star topology where devices are organized into clusters. Each cluster has a cluster head (coordinator or router) that manages communication within the cluster and with other clusters.
- Cluster Head: Acts as the coordinator for its cluster and can also relay messages to other clusters.
- End Devices: Communicate with their cluster head and do not directly interact with devices in other clusters.
- Advantages:
- Hierarchical Management: Organizes devices into manageable clusters, reducing complexity.
- Efficient Communication: Reduces the number of hops required for communication between devices in different clusters.
- Disadvantages:
- Cluster Dependency: Communication relies on the cluster heads, so if a cluster head fails, devices within that cluster may lose connectivity.

Near Filed Communication
Near Field Communication (NFC) is a short-range wireless communication technology that enables devices to exchange data over very short distances, typically up to 10 centimeters (about 4 inches). NFC is designed for ease of use and is commonly used for applications where simple, secure, and rapid communication is needed. Here’s an overview of NFC:
Key Features of NFC
- Short Range
- Range: NFC operates within a very short range, typically up to 10 cm. This short range helps ensure that communication occurs only when devices are in close proximity, enhancing security.
- Ease of Use
- Touch-Based Interaction: NFC enables easy and intuitive interaction by simply bringing devices close together or tapping them together.
- No Need for Pairing: NFC devices can communicate without the need for manual pairing or complex configuration.
- High Security
- Limited Range: The short communication range reduces the risk of unauthorized interception or eavesdropping.
- Secure Transactions: NFC is often used in secure applications like payment systems, access control, and identity verification.
Types of NFC
NFC (Near Field Communication) supports two main types of communication: passive communication and active communication. These modes define how NFC devices and tags interact with each other. Here’s an overview of each:
1. Passive Communication
Passive communication refers to the mode where one device (the NFC tag) does not require a power source and relies on the energy provided by the reader to function. The reader supplies the energy needed for the NFC tag to operate, enabling it to communicate by modulating the radio frequency (RF) field.
Characteristics of Passive Communication:
- Power Source: The NFC tag (passive device) does not have its own power source. It operates by harvesting energy from the electromagnetic field generated by the NFC reader (active device).
- Operation: The tag uses this harvested energy to power its circuits and modulate the signal back to the reader, allowing data to be transmitted.
- Communication: Data exchange is based on modulation of the RF signal. The tag does not generate its own RF field but rather responds to the reader’s signal.
- Typical Use: Commonly used in NFC tags and contactless cards. Examples include smart posters, product labels, and transit passes.
Examples of Passive NFC Communication:
- NFC Tags: Stickers or cards that contain a small amount of data. They don’t have their own power source but are activated by the reader.
- Contactless Payment Cards: Cards that can be read by payment terminals without requiring a battery or power source.
2. Active Communication
Active communication involves both devices generating their own RF fields and communicating with each other. In this mode, both devices are capable of generating their own power and can both actively send and receive data.
Characteristics of Active Communication:
- Power Source: Both devices (e.g., NFC-enabled smartphones or active tags) have their own power sources. They can generate their own RF fields and do not rely on an external source for energy.
- Operation: Both devices can initiate communication, with each device capable of transmitting and receiving data. The communication is based on the mutual exchange of RF signals.
- Communication: Allows for more complex data exchanges and interactions since both devices are active participants in the communication process.
- Typical Use: Common in NFC-enabled smartphones and devices that engage in peer-to-peer data exchange or establish connections with each other.
Examples of Active NFC Communication:
- Peer-to-Peer Communication: Two NFC-enabled smartphones exchanging files, contacts, or other data by bringing them close together.
- Device Pairing: Setting up a Bluetooth connection by tapping two NFC-enabled devices together to initiate pairing.
Summary
- Passive Communication:
- Power: Relies on energy from the reader.
- Operation: Tag modulates the reader’s signal to send data.
- Use Cases: NFC tags, contactless payment cards, smart posters.
- Active Communication:
- Power: Both devices generate their own RF fields.
- Operation: Both devices can actively send and receive data.
- Use Cases: Peer-to-peer data exchange, device pairing.
Both modes of NFC communication enable a wide range of applications, from simple data reading to complex interactions between devices, providing versatility and convenience in various scenarios.
Applications of NFC
- Contactless Payments
- Description: NFC enables secure and convenient payments by tapping a smartphone or contactless card on a payment terminal.
- Examples: Mobile payment systems like Google Pay, Apple Pay, and contactless credit/debit cards.
- Access Control
- Description: NFC can be used for secure access to buildings, rooms, or devices by tapping an NFC-enabled keycard or smartphone on a reader.
- Examples: Hotel room keys, office access cards, and smart locks.
- Smart Posters and Information Sharing
- Description: NFC tags embedded in posters, product packaging, or other items can provide additional information or link to digital content when scanned with an NFC-enabled device.
- Examples: Interactive advertising, product details, and event information.
- Pairing and Setup
- Description: NFC can simplify the process of pairing devices or setting up connections by automatically initiating the connection when devices are brought close together.
- Examples: Bluetooth pairing, Wi-Fi setup, and device configuration.
- Identification and Authentication
- Description: NFC can be used for secure identification and authentication, such as accessing secure systems or verifying identities.
- Examples: Digital IDs, access badges, and authentication tokens.
Working principle of NFC
Near Field Communication (NFC) is a wireless communication technology that enables short-range interactions between devices. It operates on the principle of inductive coupling, which allows devices to communicate when they are brought close together, typically within a range of 10 centimeters (about 4 inches). Here’s a detailed look at the working principle of NFC:
Basic Working Principle
NFC operates on the principle of electromagnetic induction. It uses radio frequency (RF) signals to enable communication between devices. The core components involved in this process are:
- Radio Frequency (RF) Field: NFC devices use an RF field to transmit and receive data. This field is generated by the antenna in the NFC device.
- Inductive Coupling: The communication between NFC devices is based on inductive coupling, where an alternating current (AC) in one device’s coil generates a magnetic field, which induces a current in the coil of the other device.
- Modulation: The data is encoded onto the RF signal through modulation techniques. The NFC device transmits data by modulating the amplitude, frequency, or phase of the RF signal. The receiving device decodes the data from the modulated signal.
Summary
NFC works by using electromagnetic induction to enable short-range communication between devices. It supports different communication modes, including passive communication (reader/tag interaction), active communication (peer-to-peer interaction), and card emulation. NFC’s operation involves generating and modulating RF fields, enabling various applications such as contactless payments, data exchange, and interactive experiences.
Modes of operations of NFC
Near Field Communication (NFC) supports several modes of operation that enable different types of interactions between devices. Each mode serves specific use cases and has distinct operational characteristics. Here’s a detailed look at the primary NFC modes of operation:
1. Reader/Writer Mode
Description: In reader/writer mode, an NFC-enabled device (the reader) interacts with an NFC tag or card (the writer). The reader can read data from or write data to the NFC tag.
Characteristics:
- One-Way Communication: The reader communicates with a passive NFC tag that does not have its own power source. The tag is powered by the energy from the reader’s RF field.
- Data Access: The reader can read information stored on the NFC tag or write new data to it if the tag supports read/write operations.
- Applications:
- Smart Posters: Users can tap their NFC-enabled device on a poster to access information or promotions.
- Product Information: Retailers can use NFC tags in product packaging to provide details or special offers.
- Interactive Labels: Tags on museum exhibits or public displays provide additional information when scanned.
2. Peer-to-Peer Mode
Description: In peer-to-peer mode, two NFC-enabled devices can communicate directly with each other. Both devices can actively send and receive data.
Characteristics:
- Two-Way Communication: Both devices generate their own RF fields and can initiate communication, allowing for bi-directional data exchange.
- Data Exchange: Devices can share files, contact information, or other data by tapping them together.
- Applications:
- File Sharing: Users can transfer files, photos, or videos between smartphones.
- Contact Exchange: Users can quickly share contact details or other information.
- Device Pairing: NFC simplifies the setup of Bluetooth or Wi-Fi connections by initiating the pairing process with a tap.
3. Card Emulation Mode
Description: In card emulation mode, an NFC-enabled device (such as a smartphone) emulates a contactless smart card. The device can be used with existing contactless card readers.
Characteristics:
- Card Emulation: The NFC device acts like a traditional contactless card, allowing it to be used in card readers for various applications.
- Data Transmission: The device communicates with the card reader using standard contactless card protocols.
- Applications:
- Contactless Payments: The device can be used for mobile payments at point-of-sale terminals by emulating a credit or debit card.
- Access Control: The device can act as an access card for secure entry to buildings or rooms.
- Public Transport: The device can be used as a transit pass for accessing public transportation systems.
Summary
NFC operates in several modes, each suited to different types of interactions:
- Reader/Writer Mode: One device (the reader) communicates with a passive NFC tag to read or write data.
- Peer-to-Peer Mode: Two active NFC devices communicate directly with each other to exchange data.
- Card Emulation Mode: An NFC device emulates a contactless smart card, enabling it to be used with existing card readers for payments or access control.
These modes enable NFC to support a wide range of applications, from simple data retrieval to complex interactions and secure transactions.
Bluetooth
Bluetooth is a wireless communication technology designed for short-range data exchange between devices. It operates in the 2.4 GHz ISM (Industrial, Scientific, and Medical) radio band and is used for various applications, from connecting peripherals to smartphones to enabling wireless audio streaming.
1. Key Features of Bluetooth
- Short-Range Communication
- Range: Typically up to 10 meters (about 33 feet) for most Bluetooth devices, though some versions and configurations can extend this range.
- Data Transfer: Designed for short-range communication with relatively low power consumption.
- Low Power Consumption
- Energy Efficiency: Bluetooth is optimized for low power usage, which is crucial for battery-operated devices.
- Bluetooth Low Energy (BLE): A variant designed specifically for very low power consumption, suitable for devices that need to operate for long periods on small batteries.
- Ease of Pairing
- Simple Setup: Devices can be paired with minimal setup and configuration, often involving just a few button presses or automatic pairing when devices are in close proximity.
- Automatic Reconnection: Once paired, devices can automatically reconnect when within range.
- Scalability
- Device Connectivity: Supports connecting multiple devices simultaneously, such as pairing a smartphone with a headset and a smart watch.
- Security
- Encryption: Bluetooth includes built-in security features, including encryption and authentication, to protect data during transmission.
Working principle of Bluetooth Technology
Bluetooth technology operates using the principles of radio frequency (RF) communication and is designed for short-range, low-power wireless data transfer. Here’s a detailed explanation of how Bluetooth works:
1. Basic Working Principle
Bluetooth communication is based on the following core principles:
a. Radio Frequency (RF) Communication
- Frequency Range: Bluetooth operates in the 2.4 GHz ISM (Industrial, Scientific, and Medical) band. This frequency range is available globally and is suitable for short-range wireless communication.
- RF Signals: Bluetooth devices use RF signals to transmit and receive data. These signals are modulated to encode the data being sent.
b. Frequency Hopping Spread Spectrum (FHSS)
- Frequency Hopping: To reduce interference from other devices using the same frequency band, Bluetooth employs frequency hopping. This involves rapidly switching the RF signal between different frequencies within the 2.4 GHz band.
- Hop Rate: Bluetooth devices hop frequencies 1,600 times per second (in Bluetooth Classic), which helps avoid interference and improves reliability.
c. Communication Channels
- Data Channels: Bluetooth divides the 2.4 GHz frequency band into 79 channels (in Bluetooth Classic) or 40 channels (in Bluetooth Low Energy). Each channel is 1 MHz wide.
- Channels: Communication occurs on these channels, with the hopping sequence ensuring that devices switch channels regularly to minimize interference and enhance connectivity.

Summary
Bluetooth technology works by utilizing radio frequency communication in the 2.4 GHz band, employing frequency hopping spread spectrum to minimize interference. It supports various communication modes, including point-to-point, point-to-multipoint, and broadcast. Pairing and connection processes ensure secure and reliable communication between devices. Bluetooth profiles define specific functionalities, and Bluetooth Low Energy (BLE) optimizes power consumption for low-energy applications. The Bluetooth stack encompasses different layers that manage the communication process, ensuring effective and efficient data exchange.
